Check the security configuration of my device
Examine your device’s security configuration for common vulnerabilities.
Check your device’s settings to see if they meet minimum recommended requirements
Device Security Scan
The Device Security Scan will look at your device and tell you what security measures you have in place and which ones you do not. These will be displayed in an easy-to-understand list.
You can use this list to determine how well your device is configured in terms of security best practice. Furthermore, implementing the missing security measures can help you improve the security of your device.
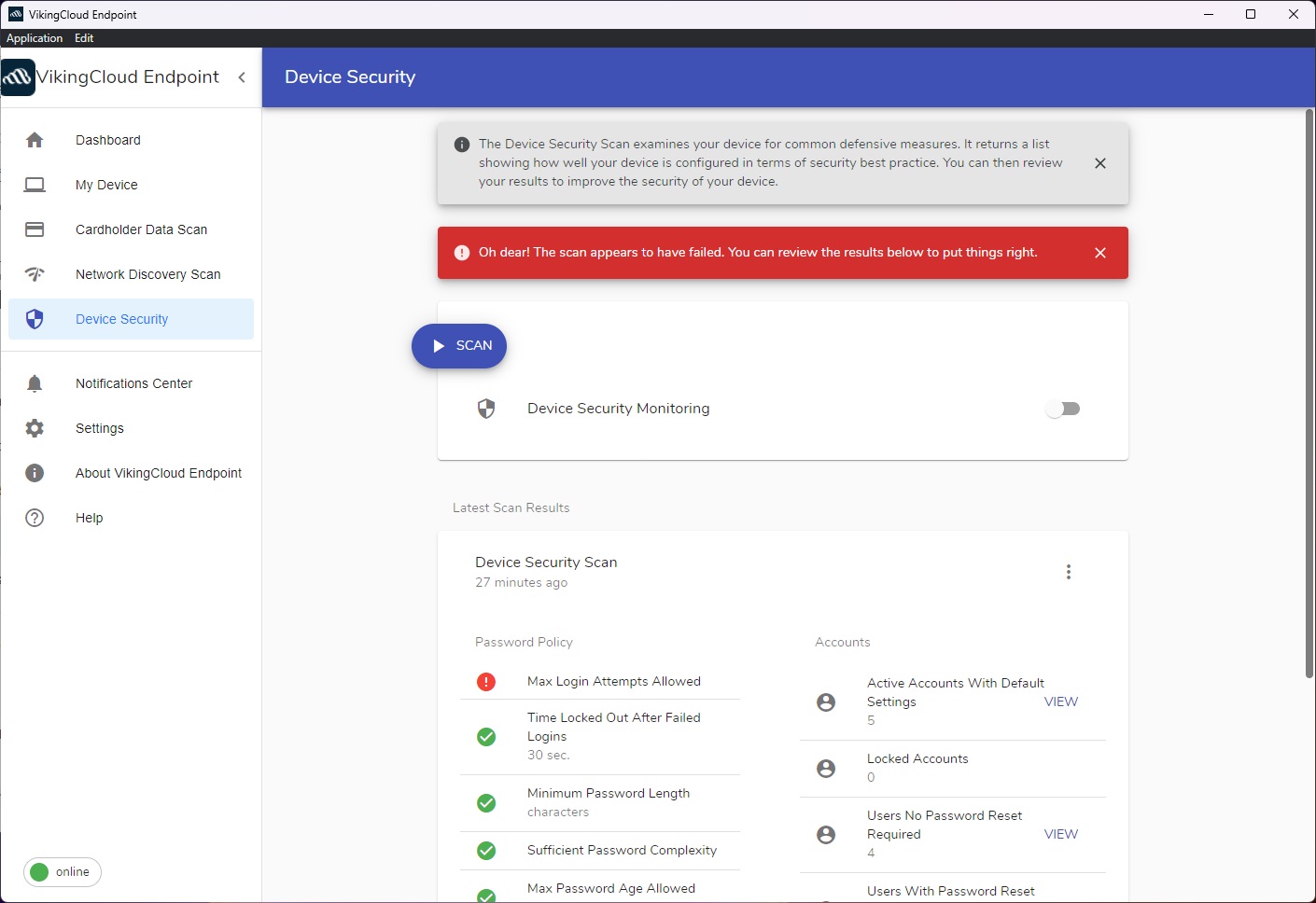
From the ‘Device Security’ tab, select ‘Scan.’ The scan will run and the results will display on the screen.
Understanding the results
Password Policy
Max login attempts allowed
What’s this? The number of times a wrong password can be entered before the user is locked out.
What’s best practice? No more than 5 failed login attempts are recommended.
Why is this important? One of the most common ways a hacker will try to access a system is by using a brute force attack. In these types of attacks the cyber criminal will repeatedly enter commonly used passwords in the hope of gaining access to your system. If your system has a policy for max login attempts along with other policies on this list, you can greatly reduce the risk of being affected by brute force attacks.
Time locked out after failed logins
What’s this? This determines how long a user will be locked out of the device for after the set number of failed log in attempts
What’s best practice? A minimum of 30 seconds is required to pass. Implementing longer lockouts is recommended, however. A longer lockout can allow administrators to assess the failed login attempts.
Why is this important? This will stop the potential hacker after a set number of attempts to log in. This will give time to an administrator to determine whether this is a genuine mistake e.g. a forgetful colleague or an attempt to breach the device in question.
Minimum password length
What’s this? This determines how many characters are needed for a password. This policy will also be required to be met when a user changes their password.
What’s best practice? 8 characters are needed to pass this section. It is best practice to have a password with a minimum of 8 characters.
Why is this important? The shorter a password is the easier said password will be to guess. For example a password with 6 characters, including only upper and lower case letters can be guessed or cracked in as little as 7 milliseconds. You can use this free tool to see how quickly a weak password can be cracked by a cyber-criminal.
Sufficient password complexity
What’s this? This determines which characters need to be included when a user creates a password.
What’s best practice? The password must contain alphabetic and numeric characters to pass. It is best practice to have a password that includes alphabetic, numeric, upper case, lower case, and special characters.
Why is this important? Much like your password length, having a complex password will make it harder for a hacker to guess your password. The hacker will now have to attempt more passwords, taking up more resources on their end. Grouping this with stricter password policies can make the hacker’s task of accessing the device very difficult.
Max password age allowed
What’s this? This determines how often a user will be prompted to change their password.
What’s best practice? Password age is required to be 90 days to pass, however changing your password every 30 days is recommended.
Why is this important? Changing passwords at regular intervals can prevent occurring or multiple ongoing breaches of a device. This policy is also useful in preventing physical breaches e.g. a disgruntled ex-employee as they may more easily guess a commonly used password by a specific user.
Unique passwords needed before reuse
What’s this? This determines how many new passwords a merchant must use before they can return to using a previously used password.
What’s best practice? 6 unique passwords are recommended before you can reuse an old password. However, reusing passwords can lead to breaches. Ideally reusing passwords should not be permitted.
Why is this important? Recurring passwords will be easier to guess especially in physical breach attempts. A common form of attack is Keylogging where the hacker will install a piece of malware which will log the keys that are entered and the order they are entered in.
Accounts
Active accounts with default settings
What’s this? This will be an account that comes store bought with default settings e.g. usernames and passwords.
What’s best practice? It is best practice to either create a brand-new user account and use unique usernames and passwords or to change the username and password on the default user account.
Why is this important? Default user accounts may well be the first thing a hacker would check before they attack your device. A google search can provide the hacker with a list of default usernames and passwords for various devices. If these accounts are on your device and you wish to keep them be sure to create a unique password and follow the above password policies.
Locked accounts
What’s this? Lists accounts on the device that are currently in a locked-out state.
What’s best practice? Locked accounts or accounts that are no longer in use should be investigated by an administrator and removed if deemed necessary.
Why is this important? Locked accounts can signify that an attempt was made to breach this device. It is important that an administrator determines whether the lockout was a genuine mistake or an attempt to breach the device.
Users with no password reset required
What’s this? This list the user accounts on your device with no max password age set.
What’s best practice? It is best practice for all user accounts on your device to have a max password age set. See “Max password age allowed” for more information.
Why is this important? This list will allow you to identify what user accounts could be a security threat to your device.
Users with password reset required
What’s this? Lists accounts that do have a max password age set.
What’s best practice? It is best practice for all user accounts on your device to have a max password age set. See “Max password age allowed” for more information.
Why is this important? By looking at this list you will be able to see which user accounts are adhering to best practices for password policies.
Where can I change these settings?
This will vary from device to device. On Mac it will typically be found in ‘Workgroup Manager’ and on Windows it will be found in ‘Local Security Policy’. Devices will vary. When managing security policies, it is always best practice to consult with an administrator or an IT professional beforehand.
System
System automatic update
What’s this? This will check whether your device has automatic updates turned on.
What’s best practice? It is best practice for a device to have automatic updates turned on and to keep up to date with the latest security updates for your operating system.
Why is this important? Having automatic updates turned on will ensure that you do not fall behind on critical security updates for your device. One of the most common ways a cyber-criminal will hack your device is through these vulnerabilities that have not yet been patched by a critical update.
Where can I change this setting? – This will vary from device to device. On windows 10 it will typically be found in settings > update and security. On windows 10, automatic updates are usually already turned on. Typically, on a mac you will need to select your apple icon > system preferences > software update and select “Automatically keep my Mac up to date”.
Antivirus installed
What’s this? This will list which antivirus software you have installed on your device.
What’s best practice? It is best practice for any device to have antivirus software installed.
Why is this important? This will allow you to verify whether you have an antivirus installed on your device. Having antivirus software installed will protect your computer from viruses and malware. Without this software, these types of files can have a negative impact on the security and performance of your computer.
Where can I change this setting? – An antivirus software will be available as part of your subscription pack and a member of security operations team will walk you through each step of the setup. It is recommended to only have one antivirus installed per device. Typically to uninstall a programme on Windows go to Control panel > Programmes > Uninstall a programme. On a Mac this is typically done by moving the application into the Trash icon. On both operating systems you may need to use an uninstall file for the software, so check with your provider.
Payment applications installed
What’s this? This will list which payment applications are currently installed on the device.
What’s best practice? If you do accept payments through a payment application, it is best practice to ensure that this is a legitimate and up to date version of the payment application.
Why is this important? Using unlicensed payment applications or accepting payments through your device without a payment application installed will leave your customer’s cardholder data in a vulnerable position.
Where can I change this setting? – Contact your payment application provider to install the latest versions.
Top articles
These are the steps to download VikingCloud Protect to your Windows device.
Read MoreCheck your device for any files that may contain un-encrypted full credit card numbers.
Read MoreExamine your device’s security configuration for common vulnerabilities.
Read More